What is Data Encryption, And How Does It Work?
What is data encryption?
Imagine sending a secret message in the olden times, but instead of ink and paper, you use a complex code only your recipient can crack. That's essentially what data encryption does in the digital realm. It's the art of transforming your confidential information into a scrambled mess, called ciphertext, that only authorised individuals with the correct key can decipher.
This key acts as a digital lock and password. Without it, even if someone intercepts the message, it appears as a jumbled mess of characters - unintelligible and useless.
How does data encryption work?
Modern encryption software employs complex algorithms and mathematical formulas to transform plain text into ciphertext.
Here’s how:
The algorithm: These are sets of rules and procedures that dictate how data is transformed from its original form to an encrypted state.
Imagine swapping all the letters in your email with random symbols; that's basically what happens.
The encryption key: The key is another special code, different from the scrambling code used in Stage 1. Only someone with the right key can unlock the ciphertext and turn it back into plain text.
It's like a password for the code, a unique set of numbers that tells the algorithm how to unscramble the mess back into readable information.
Secure transmission: Your encrypted data, disguised as ciphertext, travels safely through the internet or any other network.
It's like sending your secret message in a sealed box, hidden in plain sight.
Key exchange: The next step is to securely exchange the encryption key without exposing it to potential threats. This is where key exchange protocols come into play. These protocols ensure that only the intended recipient possesses the key, preventing unauthorised access.
It's like passing a secret baton in a relay race – only the trusted runner (recipient) can unlock the encrypted message.
Authentication: Authentication ensures that the sender and receiver are who they claim to be, preventing impostors from slipping through the cracks.
Think of it as a digital handshake – a mutual confirmation that the encrypted message hasn't been tampered with during transmission. By verifying the identities of both parties, authentication adds an extra layer of trust to the encryption process.
The primary function of data encryption
Data encryption safeguards personal information, protects intellectual property, and ensures compliance with data privacy regulations like GDPR and HIPAA. By ensuring confidentiality and integrity, encryption builds trust and strengthens your relationships with customers and partners.
The fundamental purpose of data encryption is to act as a silent guardian, ensuring only authorised individuals can access sensitive information, regardless of its location – be it stored on your servers, transmitted over the internet, or residing in a cloud storage environment.
Encryption is crucial for protecting:
Personal information like names, addresses, and other sensitive data that deserve the utmost protection from identity theft and fraud.
Financial data such as credit card numbers, bank account details, and financial transactions that are prime targets for cybercriminals.
Intellectual property including trade secrets, business plans, and other confidential information that must be safeguarded from competitors and industrial espionage.
The role of encryption keys in securing data
The security of encrypted data hinges on the keys used for encryption and decryption. These keys, essentially strings of random characters, act like the teeth of a comb, meticulously fitting into the specific grooves created by the chosen encryption algorithm. The stronger the decryption key, the more complex the grooves, making it exponentially harder for unauthorised parties to crack the code.
There are several types of encryption keys, each serving a specific purpose in the encryption process.
Symmetric key: This is a single key that transforms plaintext into ciphertext during encryption and reverses the process during decryption.
Use cases: Commonly used for real-time application and bulk data encryption, such as securing files and communication.
Asymmetric keys: These are pairs of public and private keys. Any party can use the public key to encrypt data before sending it to the owner of the corresponding private key. The public keys can be freely distributed, eliminating the need for secure key exchange. However, protecting the private key is crucial.
Use cases: Primarily used for secure communication, digital signatures, and key exchange in protocols like SSL/TLS.
Session keys: In many secure communication protocols, especially those over the internet, a unique session key is generated for each session. This session key is often derived from a combination of symmetric and asymmetric encryption.
Use cases: Helps in securing individual communication sessions, providing forward secrecy by generating unique keys for each session.
Hashing keys: Hash functions use keys to create a fixed-size hash value or checksum for a given set of data. Hashing is not reversible, and even a small change in the input data produces a significantly different hash value.
Use cases: Used for data integrity verification, password storage (hashed passwords), and digital signatures.
Key derivation keys: Key derivation functions are used to derive one or more secret keys from a single secret value or password. This is often done to enhance security by avoiding the direct use of passwords as encryption keys.
Use cases: Protects against certain types of attacks, such as brute force attacks on password-based systems.
Initialisation vectors (IVs): IVs are used alongside encryption algorithms to ensure that the same plaintext does not encrypt to the same ciphertext every time. They add randomness to the encryption process.
Use cases: Essential for securing data with block ciphers, especially in modes like CBC (Cipher Block Chaining).
Proper cryptographic key management, including key generation, distribution, storage, and rotation, is crucial for maintaining the security of encrypted data. Additionally, the security of the entire system relies on protecting the confidentiality and integrity of the keys.
Data encryption vs database encryption
Data encryption is the process of converting plain, readable data into an unreadable format using algorithms and cryptographic keys.
Database encryption involves either encrypting data from the entire database or specific fields within it to protect the stored information.
|
Data encryption |
Database encryption |
Scope |
Primarily focuses on securing data during transmission or on devices. |
Protects data stored within a database, whether at rest or during access. |
Level of granularity |
Works on individual files or messages. |
Operates at a higher level, encrypting entire databases or specific columns. |
Use cases |
Ideal for securing data during communication or on individual devices. |
Essential for protecting comprehensive databases and meeting regulatory requirements. |
Both the data encryption algorithms and database encryption are indispensable tools in the fight against cyber threats.
While data encryption ensures secure data transfer and storage on devices, database encryption takes a holistic approach to safeguarding stored data.
Employing a combination of both techniques provides a multi-layered security strategy, fortifying your organisation against the evolving landscape of digital threats.
Understanding the risks of data breaches
A data breach occurs when unauthorised individuals gain access to sensitive and confidential information. These breaches pose significant risks and can lead to severe consequences for you, your business, and its stakeholders. Also, handling customer inquiries and complaints after a breach can strain customer support resources.
The average cost of a data breach is $4.35 million, with 83% of organisations having multiple breaches!
Financial loss: You may incur expenses related to investigating the breach, notifying affected parties, and implementing security measures. 34.5% of polled executives report that their organisations' accounting and financial data were targeted by cyber adversaries.
Reputation damage: Your customers and stakeholders may lose trust in your organisation if you fail to protect their data. And a tarnished reputation can take years to rebuild, impacting customer loyalty and market standing.
Identity and IP (Intellectual Property) theft: Cyber criminals may steal personal data to open fraudulent accounts, make unauthorised purchases, or commit other financial crimes. Similarly, if data protection measures are ineffective, you risk the theft of proprietary information, compromising your competitive edge. Fear of intellectual property theft may hinder innovation and research efforts.
Legal consequences: Non-compliance with data protection regulations may result in hefty regulatory fines for your organisation. And individuals affected by a breach may pursue legal action against you for negligence.
Operational disruption: Remediation efforts, investigations, and recovery can disrupt your normal business operations. Your workforce may be preoccupied with addressing the breach, leading to decreased productivity.
Supply chain impact: A breach in your organisation can have a cascading effect, affecting your partners and suppliers. Interruptions in the supply chain may lead to delays and financial losses for interconnected businesses.
Proactive data protection strategies, including encryption, access controls, and regular security audits, are crucial in mitigating the risks associated with data breaches and preserving the integrity of sensitive information.
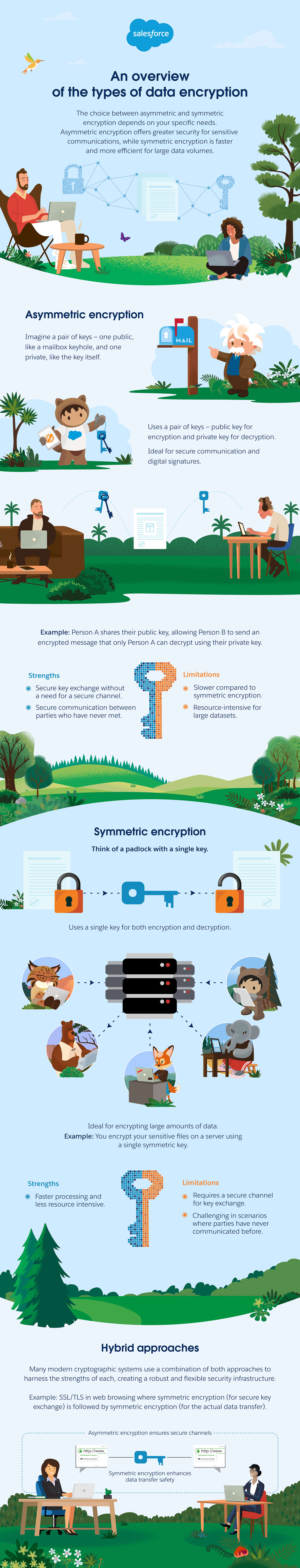
Types of data encryption: asymmetric vs. symmetric
Asymmetric and symmetric encryption represent two distinct approaches, each with its advantages and use cases.
An overview of the types of data encryption
The choice between asymmetric and symmetric encryption depends on your specific needs. Asymmetric encryption offers greater security for sensitive communications, while symmetric encryption is faster and more efficient for large data volumes.
Asymmetric encryption
Imagine a pair of keys – one public, like a mailbox keyhole, and one private, like the key itself.
Uses a pair of keys - public key for encryption and private key for decryption.
Ideal for secure communication and digital signatures.
Example: Person A shares their public key, allowing Person B to send an encrypted message that only Person A can decrypt using their private key.Strengths:
Secure key exchange without a need for a secure channel.
Secure communication between parties who have never met.
Limitations:
Slower compared to symmetric encryption.
Resource-intensive for large datasets.
Symmetric encryption
Think of a padlock with a single key.
Uses a single key for both encryption and decryption.
Ideal for encrypting large amounts of data.
Example: You encrypt your sensitive files on a server using a single symmetric key.Strengths: Faster processing and less resource intensive.
Limitations:
Requires a secure channel for key exchange.
Challenging in scenarios where parties have never communicated before.
Hybrid approaches
Many modern cryptographic systems use a combination of both approaches to harness the strengths of each, creating a robust and flexible security infrastructure.
Example: SSL/TLS in web browsing where symmetric encryption (for secure key exchange) is followed by symmetric encryption (for the actual data transfer).
Benefits of data encryption
Data encryption is essential for data confidentiality, integrity, trust and reputation, and prevention of insider threats. It safeguards digital exchanges by ensuring:
Protection from unauthorised access and data theft. Only authorised individuals with the correct keys can access sensitive information.
Protection during data transmission, enhancing confidentiality in professional and business communications.
Compliance with data protection regulations like GDPA and HIPAA.
Data integrity by preventing unauthorised modifications. Any attempt to tamper with encrypted data would result in unreadable content, alerting the user to potential tampering.
Your commitment to securing user data, which helps build trust among customers, clients, and partners.
Risk mitigation associated with insider threats by restricting access to data even for employees within your organisation. Insider risks account for 25% of data breaches, involving current and former employees, associates, and contractors.
Protection of stored data. Even if physical devices (such as hard drives or databases) are stolen, the data remains unreadable without the appropriate decryption keys.
Security of data residing on cloud servers.
Flexibility and adaptability so you can tailor encryption strategies to different types of information such as files, emails, databases, and communication channels.
Challenges to contemporary encryption
The dynamic nature of cyber threats poses a significant challenge to contemporary data encryption solutions. The rising cost of damages resulting from cybercrime is expected to reach $10.5 trillion by 2025.
As technology advances, so do the tactics employed by malicious actors, ranging from sophisticated hacking techniques to social engineering.
This evolving landscape demands constant vigilance to ensure the effectiveness of encryption measures.
The most pressing challenges to current encryption methods include:
Key management: Weak key management practices can render encryption ineffective and compromise data security.
Encryption backdoors: Encryption backdoors, which allow law enforcement access to encrypted data, raises concerns about privacy and security implications.
Vulnerability of encryption algorithms: Over time, cryptanalysis techniques may reveal weaknesses in existing encryption algorithms. This necessitates continuous research and development to stay ahead of the curve.
Social engineering attacks: Hackers may try to trick users into revealing their decryption keys or granting access to encrypted data. Proper security awareness training is crucial to mitigate such risks.
Continuous innovation, updates, and thoughtful considerations in policy and technology are essential to navigating this complex landscape and ensuring the ongoing effectiveness of encryption in safeguarding sensitive information.
In the next section, we elaborate on what you can do to ensure effective data encryption.
Effective data encryption
As you navigate the evolving landscape of cyber threats, adopting encryption is not enough. You must embrace a comprehensive strategy that spans the entire lifecycle of data. From its inception to the moment it is accessed in real-time and during its transit across networks, you need a shield for every facet of the data.
Here’s what you can do:
Choose encryption algorithms with strong key sizes and proven track records against known vulnerabilities.
NIST (National Institute of Standards and Technology) provides guidance on recommended algorithms for secure data protection. It is also standardising algorithms for post quantum encryption and lightweight cryptography. These are designed to
a. Resist attacks by quantum computers.
b. Protect data created and transmitted by the Internet of Things and other small electronics.
Implement robust key management protocols.
Consider dedicated key management solutions including secure key generation, storage, encryption key management and distribution for centralised control and enhanced security.
Encrypt across the data lifecycle.
Don't limit encryption to just data at rest. Include data in transit (e.g., emails, file transfers) and data in use (e.g., databases with real-time access) for comprehensive protection.
Conduct regular security awareness training
It is vital to educate employees on the importance of data security and best practices for handling encrypted information.
Stay informed about emerging threats and vulnerabilities in the encryption landscape.
Regularly update your encryption methods and key management practices to stay ahead of cybercriminals.
Future trends in data security
Forget outdated firewalls and static defences. The future of data security lies in dynamic anticipation, adaptation, and relentless innovation. Think of it as a high-stakes game of chess, where we not only react to our opponent's moves but predict them. The goal is to take proactive measures that outmanoeuvre even the most cunning threats.
Here are the trends to watch out for:
Zero-trust security models
The zero-trust approach asks you to assume no one is trustworthy to enter spaces, crawl through tunnels, or breach walls until they have continuously proven their identity for each associated level of access. This involves moving beyond perimeter defences to a continuous authentication and authorisation process, even within trusted networks.
Quick tips:
- Adopt multi-factor authentication, micro-segmentation, and continuous monitoring.
AI-powered security
AI in the cybersecurity market is expected to reach a market value of $46.3 billion in 2027. AI and machine learning will evolve to detect and prevent threats in real-time, automate incident response, and predict future attacks.
Quick tips:
Use AI-powered tools to analyse encryption patterns and data access logs to identify anomalies and potential threats.
- Invest in security platforms with AI capabilities and train your teams on interpreting and utilising AI outputs.
Quantum-resistant cryptography
While still in its infancy, quantum computing poses a significant threat to current encryption methods. Quantum-resistant cryptography will be a rising area of research and development to future-proof data security.
Quick tips:
Develop a long-term data security strategy that accounts for the evolution of quantum computing.
Engage in collaborative efforts with industry peers, researchers, and cybersecurity experts to stay ahead of quantum threats.
- Stay informed about advancements in quantum-resistant cryptography and be prepared to update encryption standards accordingly to maintain robust data protection measures.
Greater emphasis on mobile and cloud security
Mobile devices, with their vast data storage and access to sensitive information, will continue to be a prime target for attackers.
Quick tips:
Implement mobile device security policies, use secure apps, and educate employees on mobile security practices.
Prioritise cloud security and implement zero-trust configurations.
Data encryption with Salesforce's Shield Platform Encryption
Data security is no longer a "nice-to-have," it's a critical line of defence in today's digital landscape. Salesforce offers cutting-edge solutions to future-proof your data encryption.
With Salesforce Shield Platform Encryption, you can:
Natively encrypt your most sensitive data at rest across all your Salesforce apps.
Encrypt data stored in many standard and custom fields and in files and attachments or data in Salesforce search indexes using an advanced HSM-based key derivation system. You can also encrypt individual fields and apply different encryption schemes to those fields.
Add an extra layer of protection to PII, sensitive, confidential, or proprietary data. So, it’s protected even when other lines of defence are compromised.
Meet external and internal data compliance policies while keeping critical app functionality such as search, workflow, and validation rules.
Ensure full control over encryption keys and can set encrypted data permissions to protect sensitive data from unauthorised users.
Choose how you want to implement encryption policies.
Salesforce is constantly adding more fields and files to the Shield Platform Encryption fold, ensuring your data fortress remains impregnable.
Explore how Salesforce Shield Platform Encryption can be your steadfast ally in comprehending data protection landscapes, elevating security performance, and establishing enduring trust with stakeholders.
Watch the free demo.

Webinar
How to Unlock Data Silos with MuleSoft and AI

Guide
How to enhance your data security and governance using the Salesforce Platform
More resources

Article

Research and Report

Article